Microsoft’s Defender Vulnerability Management is a built-in module in Microsoft Defender for Endpoint that can:
- Discover vulnerabilities and misconfigurations in near real time
- Prioritize vulnerabilities based on the threat landscape and detections in your organization
If you’ve enabled the integration with Microsoft Defender for Endpoint, you’ll automatically get the Defender Vulnerability Management findings without the need for more agents.
As it’s a built-in module for Microsoft Defender for Endpoint, Defender Vulnerability Management doesn’t require periodic scans.
In case you have started to use Qualys vulnerability assessment as part of Defender for Cloud, and you now wants to switch to use Defender for Vulnerability management instead, it is currently not supported to handle the migration from Qualys to MdeTvm by policies. This is why I made this blog, as it automates the disabling of Qualys and onboarding to MdeTvm in an automated approach using REST api.
Removing the Qualys extension is not enough, as we still need to turn off the integration in the api.
Onboarding your machines to Defender Vulnerability Management
If you have never used any vulnerability assessment tool, it is pretty easy to get started.
The integration between Microsoft Defender for Endpoint and Microsoft Defender for Cloud takes place in the background, so it doesn’t involve any changes at the endpoint level.
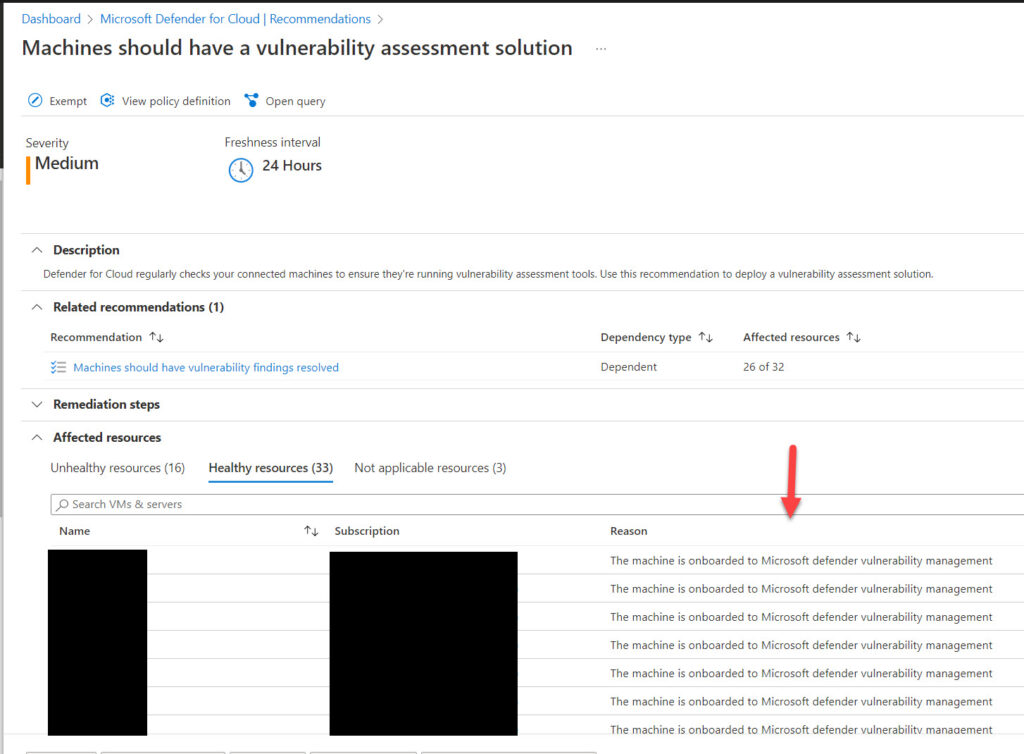
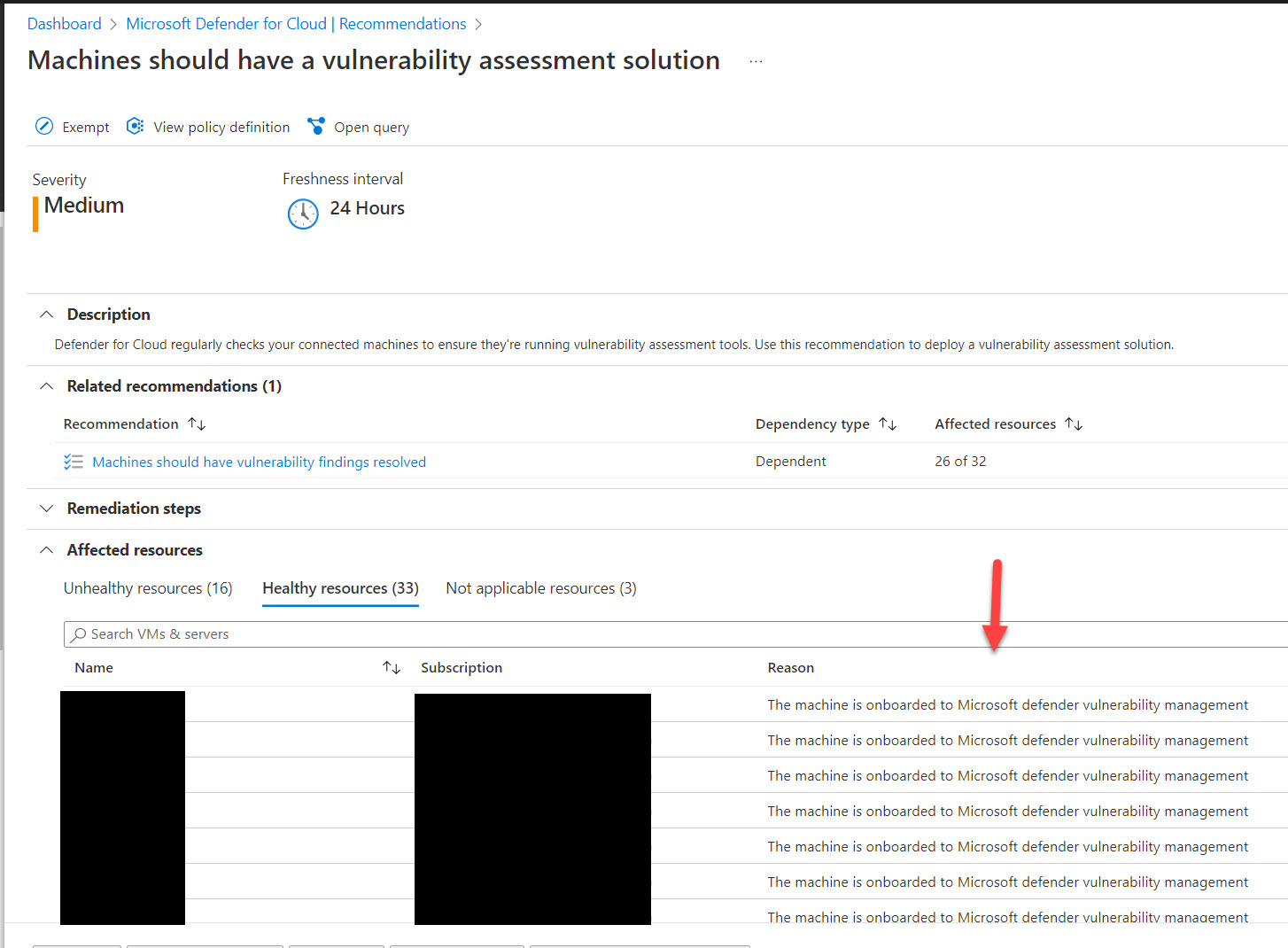
- To manually onboard one or more machines to Defender Vulnerability Management, use the security recommendation “Machines should have a vulnerability assessment solution“:
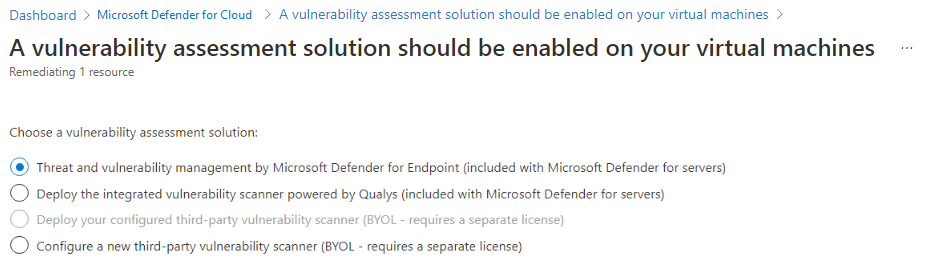
- To automatically find and view the vulnerabilities on existing and new machines without the need to manually remediate the preceding recommendation, see Automatically configure vulnerability assessment for your machines.
- To onboard via the REST API, run PUT/DELETE using this URL:
https://management.azure.com/subscriptions/.../resourceGroups/.../providers/Microsoft.Compute/virtualMachines/.../providers/Microsoft.Security/serverVulnerabilityAssessments/mdetvm?api-version=2015-06-01-preview
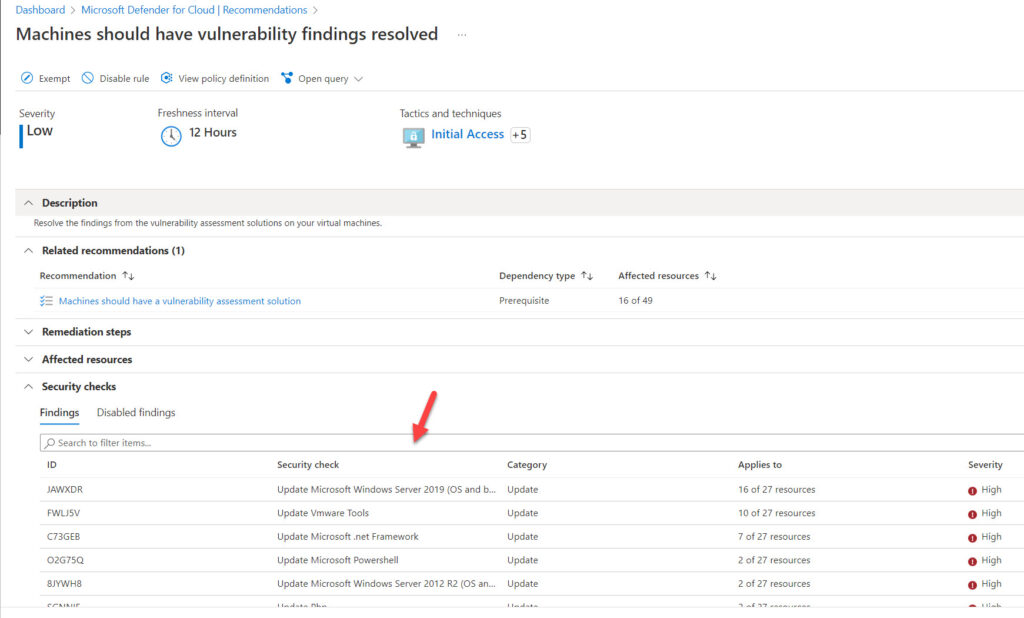
The findings for all vulnerability assessment tools are in the Defender for Cloud recommendation Vulnerabilities in your virtual machines should be remediated. Learn about how to view and remediate findings from vulnerability assessment solutions on your VMs
Migration from Qualys to MdeTvm
If you are currently using Qualys as your vulnerability assessment tool, I have provided a script on my github to assist in the migration away from Qualys to MdeTvm using REST api method
The script includes an advanced method to do proper targeting with support to exclude subscriptions, resource groups, resources with advanced filtering capabilities.
The main program of the script is shown below
$MdeTvmArray = @()
$QualysArray = @()
ForEach ($VM in $Global:Scope_Computer_Array)
{
Write-Output ""
Write-Output "Checking $($Vm.ComputerName) for vulnerability assessment solution ... Please Wait !"
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments?api-version=2015-06-01-preview"
$VA_Status = Invoke-RestMethod $uri -Method GET -Headers $Header -ContentType "application/json" -ErrorAction SilentlyContinue
# Check if VM has been enabled with Qualys as Server Vulnerability Assessment solution
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments/default?api-version=2015-06-01-preview"
Try
{
$StatusQualys = Invoke-RestMethod $uri -Method GET -Headers $Header -ContentType "application/json" -ErrorAction SilentlyContinue
}
Catch
{
}
$QualysArray += $StatusQualys
If ($StatusQualys.properties.provisioningState -eq "Succeeded")
{
Write-Output " Deprovisioning Qualys Vulnerability Assessment on resource $($Computer)"
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments/default?api-version=2015-06-01-preview"
$Delete = Invoke-RestMethod $uri -Method DELETE -Headers $Header -ContentType "application/json" -ErrorAction SilentlyContinue
}
# Check if VM has been enabled for MdeTvm as Server Vulnerability Assessment solution
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments/mdetvm?api-version=2015-06-01-preview"
Try
{
$StatusMdeTvm = Invoke-RestMethod $uri -Method GET -Headers $Header -ContentType "application/json" -ErrorAction SilentlyContinue
}
Catch
{
Write-Output " Enabling MdeTvm Vulnerability Assessment on $($Computer)"
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments/mdetvm?api-version=2015-06-01-preview"
$Update = Invoke-RestMethod $uri -Method PUT -Headers $Header -ContentType "application/json"
}
$MdeTvmArray += $StatusMdeTvm
If ( ($StatusMdeTvm.properties.provisioningState -eq "Succeeded") -and ($StatusMdeTvm.name -eq "MdeTvm") )
{
Write-Output " MdeTvm Vulnerability Assessment solution already enabled on resource $($Computer) ... skipping !"
}
Elseif ( (!$StatusQualys) -and (!$StatusMdeTvm) )
{
Write-Output ""
Write-Output " Enabling MdeTvm Vulnerability Assessment on $($Computer)"
$Uri = "https://management.azure.com$($VM.Id)/providers/Microsoft.Security/serverVulnerabilityAssessments/mdetvm?api-version=2015-06-01-preview"
$Update = Invoke-RestMethod $uri -Method PUT -Headers $Header -ContentType "application/json"
}
}
Good write up. Did you run into machines not reporting in healthy after? About 30% completed successfully, the rest are now unhealthy.
Yes I have seen this when the provisioningState of the Qualys (default) were in failed state – could be seen using a GET. A DELETE didn’t remove it.
Solution was to do the following on the impacted machines:
1) do a PUT on the Qualys. Now extension will be deployed and you are re-enabling qualys
2) wait 10-15 min to let it settle down
3) do a new DELETE and now it will gævhange state to deprovisioning
4) remove the SecurityCenter extension from the machine
Now they will most likely be in a healthy state.
Nice stuff!
But, how about the other way around: moving from Microsoft to Qualys?
Sascha
@sascha, haven’t tried that in big scale as my customers are happy with MS, but I guess the steps are:
1) offboard MDE using offboard script
2) remove MDE extension
3) run a DELETE in the api for MdeTvm
4) run a PUT for the default (qualys). It will trigger extension install
Thanks for this,what are the licence requirement moving from.Qualys to MDETVM? As not all the Qualys server has MDE for access to Defender for server
No license req
https://learn.microsoft.com/en-us/azure/defender-for-cloud/deploy-vulnerability-assessment-vm
It does say in that document, requires Microsoft Defender for Servers Plan 2. They are looking to include Azure Arc enabled devices.
Yes, but its not a license. It is a payable subscription on monthly basis which includes qualys. You can also buy qualys separately with byol